KAGOYAクラウドと自宅、それぞれのvyos同士をsite to site vpn方式で接続する。
また、自宅はポート開放されておらず、SourceNAT形式でインターネットへ出るため、その考慮が必要。
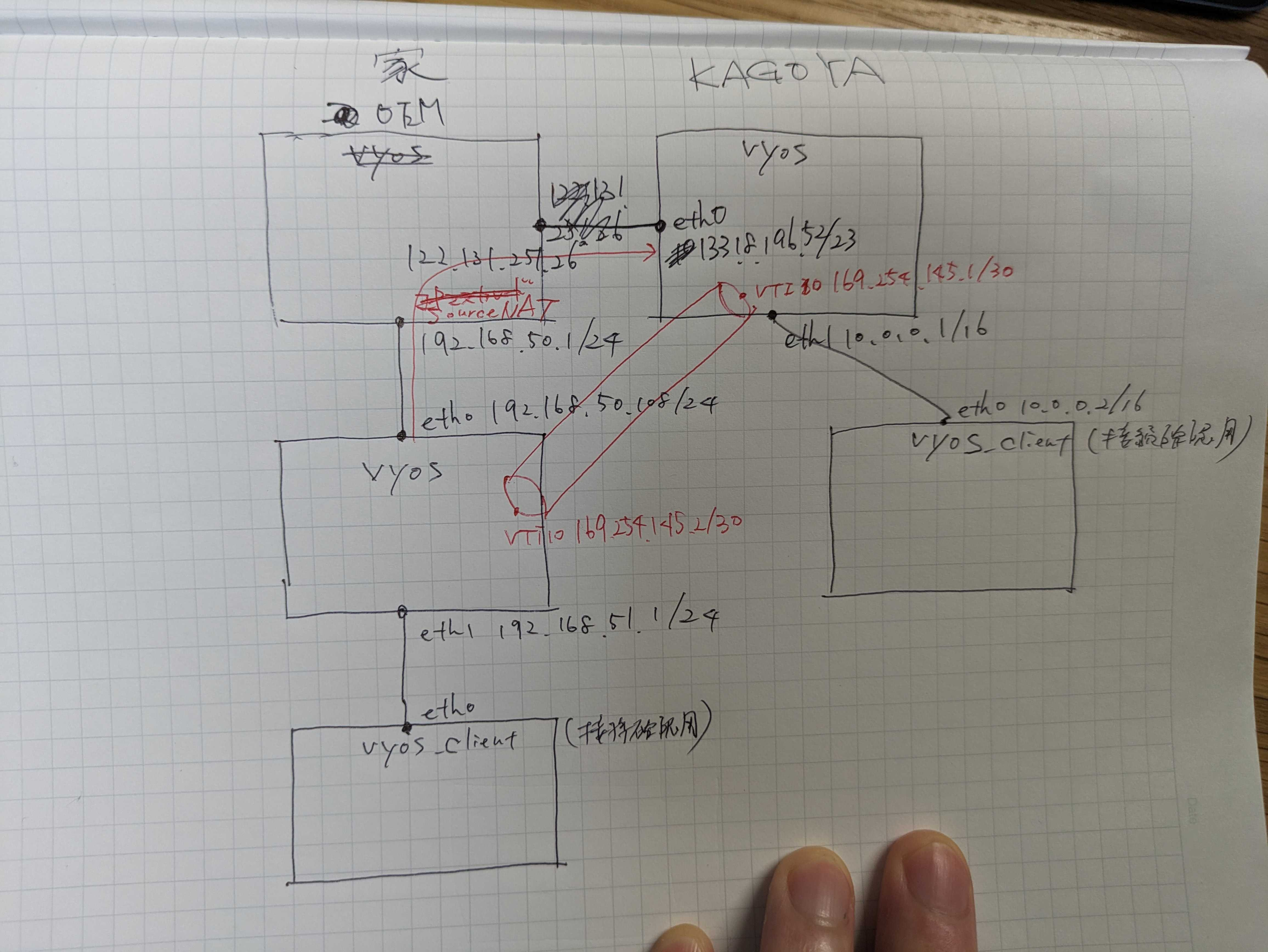
KAGOYA側vyos
set vpn ipsec esp-group MyESPGroup proposal 1 encryption 'aes128' set vpn ipsec esp-group MyESPGroup proposal 1 hash 'sha1' set vpn ipsec ike-group MyIKEGroup proposal 1 dh-group '2' set vpn ipsec ike-group MyIKEGroup proposal 1 encryption 'aes128' set vpn ipsec ike-group MyIKEGroup proposal 1 hash 'sha1' set vpn ipsec site-to-site peer 133-18-196-52 authentication mode 'pre-shared-secret' set vpn ipsec authentication psk vyos id 133.18.196.52 set vpn ipsec authentication psk vyos secret '666' set vpn ipsec site-to-site peer 133-18-196-52 authentication local-id '133.18.196.52' set vpn ipsec site-to-site peer 133-18-196-52 local-address '133.18.196.52' set vpn ipsec site-to-site peer 133-18-196-52 connection-type 'respond' # VPNサーバ側になる方にrespond set vpn ipsec site-to-site peer 133-18-196-52 ike-group 'MyIKEGroup' set interfaces vti vti10 address '169.254.145.1/30' set vpn ipsec site-to-site peer 133-18-196-52 vti bind 'vti10' set vpn ipsec site-to-site peer 133-18-196-52 vti esp-group 'MyESPGroup' set vpn ipsec site-to-site peer 133-18-196-52 remote-address 122.131.251.26 set vpn ipsec option disable-route-autoinstall
必須ではないけどDHCP設定をする
set service dhcp-server hostfile-update set service dhcp-server shared-network-name NET-VYOS subnet 10.0.0.0/16 option default-router '10.0.0.1' set service dhcp-server shared-network-name NET-VYOS subnet 10.0.0.0/16 option name-server '8.8.8.8' set service dhcp-server shared-network-name NET-VYOS subnet 10.0.0.0/16 option domain-name 'vyos.net' set service dhcp-server shared-network-name NET-VYOS subnet 10.0.0.0/16 range 0 start '10.0.1.1' set service dhcp-server shared-network-name NET-VYOS subnet 10.0.0.0/16 range 0 stop '10.0.1.254' set service dhcp-server shared-network-name NET-VYOS subnet 10.0.0.0/16 subnet-id '1'
自宅側vyos
set vpn ipsec esp-group MyESPGroup proposal 1 encryption 'aes128' set vpn ipsec esp-group MyESPGroup proposal 1 hash 'sha1' set vpn ipsec ike-group MyIKEGroup proposal 1 dh-group '2' set vpn ipsec ike-group MyIKEGroup proposal 1 encryption 'aes128' set vpn ipsec ike-group MyIKEGroup proposal 1 hash 'sha1' set vpn ipsec site-to-site peer 122-131-251-26 authentication mode 'pre-shared-secret' set vpn ipsec authentication psk vyos id 122.131.251.26 set vpn ipsec authentication psk vyos secret '666' set vpn ipsec site-to-site peer 122-131-251-26 authentication local-id '122.131.251.26' set vpn ipsec site-to-site peer 122-131-251-26 authentication remote-id '133.18.196.52' set vpn ipsec site-to-site peer 122-131-251-26 local-address '192.168.50.108' set vpn ipsec site-to-site peer 122-131-251-26 remote-address '133.18.196.52' set vpn ipsec site-to-site peer 122-131-251-26 connection-type 'initiate' set vpn ipsec site-to-site peer 122-131-251-26 ike-group 'MyIKEGroup' set interfaces vti vti10 address '169.254.145.2/30' set vpn ipsec site-to-site peer 122-131-251-26 vti bind 'vti10' set vpn ipsec site-to-site peer 122-131-251-26 vti esp-group 'MyESPGroup' set vpn ipsec option disable-route-autoinstall
こちら側もDHCP設定をしておく
set service dhcp-server hostfile-update set service dhcp-server shared-network-name NET-VYOS subnet 192.168.51.0/24 option default-router '192.168.51.1' set service dhcp-server shared-network-name NET-VYOS subnet 192.168.51.0/24 option name-server '8.8.8.8' set service dhcp-server shared-network-name NET-VYOS subnet 192.168.51.0/24 option domain-name 'vyos.net' set service dhcp-server shared-network-name NET-VYOS subnet 192.168.51.0/24 range 0 start '192.168.51.101' set service dhcp-server shared-network-name NET-VYOS subnet 192.168.51.0/24 range 0 stop '192.168.51.200' set service dhcp-server shared-network-name NET-VYOS subnet 192.168.51.0/24 subnet-id '1'
設定完了したら、restart allまたはrebootして、設定を反映させる。
Stateがupになっていれば、ipsecの接続は完了している。
ちなみに、NAT-Tはinitiate側はyes,respond側はnoになる。
vyos@vyos:~$ show vpn ike sa
Peer ID / IP Local ID / IP
------------ -------------
133.18.196.52 133.18.196.52 192.168.50.108 122.131.251.26
State IKEVer Encrypt Hash D-H Group NAT-T A-Time L-Time
----- ------ ------- ---- --------- ----- ------ ------
up IKEv2 AES_CBC_128 HMAC_SHA1_96 MODP_1024 yes 10 27727
vyos@vyos:~$ show vpn ipsec sa
Connection State Uptime Bytes In/Out Packets In/Out Remote address Remote ID Proposal
------------------ ------- -------- -------------- ---------------- ---------------- ------------- ------------------------
122-131-251-26-vti up 49s 0B/0B 0/0 133.18.196.52 133.18.196.52 AES_CBC_128/HMAC_SHA1_96
ipsecが確立していれば、それぞれがそれぞれのvtiのIPアドレスにpingが届くはず。
ここまでいけば、あとはルーティングの話になる。
vyos@vyos:~$ ping 169.254.145.1 count 3 PING 169.254.145.1 (169.254.145.1) 56(84) bytes of data. 64 bytes from 169.254.145.1: icmp_seq=1 ttl=64 time=11.4 ms 64 bytes from 169.254.145.1: icmp_seq=2 ttl=64 time=11.3 ms 64 bytes from 169.254.145.1: icmp_seq=3 ttl=64 time=11.4 ms --- 169.254.145.1 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2003ms rtt min/avg/max/mdev = 11.278/11.341/11.386/0.045 ms
KAGOYAサーバ側にBGP設定を入れる。
# vyos側 set protocols bgp system-as 65002 set protocols bgp neighbor 169.254.145.2 remote-as 65001 set protocols bgp neighbor 169.254.145.2 address-family ipv4-unicast soft-reconfiguration inbound set protocols bgp neighbor 169.254.145.2 update-source 169.254.145.1 set protocols bgp timers holdtime 30 set protocols bgp timers keepalive 10 # 対抗側に経路宣伝する set protocols bgp address-family ipv4-unicast network 10.0.0.0/16
自宅側にもBGP設定を入れる。
# vyos側 set protocols bgp system-as 65001 set protocols bgp neighbor 169.254.145.1 remote-as 65002 set protocols bgp neighbor 169.254.145.1 address-family ipv4-unicast soft-reconfiguration inbound set protocols bgp neighbor 169.254.145.1 update-source 169.254.145.2 set protocols bgp timers holdtime 30 set protocols bgp timers keepalive 10 # 対抗側に経路宣伝する set protocols bgp address-family ipv4-unicast network 192.168.51.0/24
それぞれ、BGP設定を確認する。
vyos@vyos:~$ show ip bgp summary
IPv4 Unicast Summary (VRF default):
BGP router identifier 192.168.51.1, local AS number 65001 vrf-id 0
BGP table version 2
RIB entries 3, using 288 bytes of memory
Peers 1, using 20 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
169.254.145.1 4 65002 13 13 2 0 0 00:01:27 1 2 N/A
Total number of neighbors 1
vyos@vyos:~$
vyos@vyos:~$ show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
t - trapped, o - offload failure
S>* 0.0.0.0/0 [1/0] via 192.168.50.1, eth0, weight 1, 06:51:13
B>* 10.0.0.0/16 [20/0] via 169.254.145.1, vti10, weight 1, 00:01:28
C>* 169.254.145.0/30 is directly connected, vti10, 06:51:09
C>* 192.168.50.0/24 is directly connected, eth0, 06:51:13
C>* 192.168.51.0/24 is directly connected, eth1, 02:21:50
vyos@vyos:~$
vyos@vyos:~$ show ip bgp summary
IPv4 Unicast Summary (VRF default):
BGP router identifier 133.18.196.52, local AS number 65002 vrf-id 0
BGP table version 2
RIB entries 3, using 288 bytes of memory
Peers 1, using 20 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
169.254.145.2 4 65001 11 11 2 0 0 00:01:02 1 2 N/A
Total number of neighbors 1
vyos@vyos:~$
vyos@vyos:~$ show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
t - trapped, o - offload failure
S>* 0.0.0.0/0 [1/0] via 133.18.196.1, eth0, weight 1, 06:56:48
C>* 10.0.0.0/16 is directly connected, eth1, 06:56:48
C>* 133.18.196.0/23 is directly connected, eth0, 06:56:48
C>* 169.254.145.0/30 is directly connected, vti10, 06:50:45
B>* 192.168.51.0/24 [20/0] via 169.254.145.2, vti10, weight 1, 00:01:03
あとは、それぞれのVPNサーバにぶら下がっているクライアントからpingが届くかを確認する。
vyos@vyos:~$ show interfaces
Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down
Interface IP Address MAC VRF MTU S/L Description
----------- ----------------- ----------------- ------- ----- ----- -------------
eth0 192.168.51.101/24 00:15:5d:0b:b3:37 default 1500 u/u
lo 127.0.0.1/8 00:00:00:00:00:00 default 65536 u/u
::1/128
vyos@vyos:~$
vyos@vyos:~$ ping 10.0.1.1 count 3
PING 10.0.1.1 (10.0.1.1) 56(84) bytes of data.
64 bytes from 10.0.1.1: icmp_seq=1 ttl=62 time=12.1 ms
64 bytes from 10.0.1.1: icmp_seq=2 ttl=62 time=11.9 ms
64 bytes from 10.0.1.1: icmp_seq=3 ttl=62 time=12.5 ms
--- 10.0.1.1 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 11.939/12.166/12.467/0.221 ms