設定
Ruleとして追加する
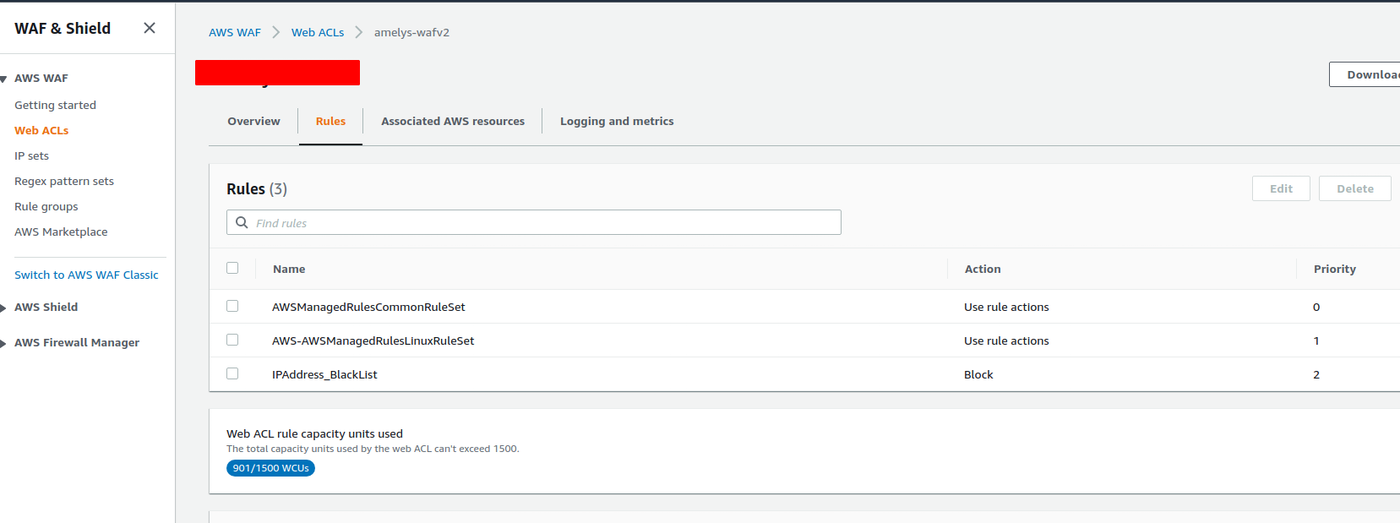
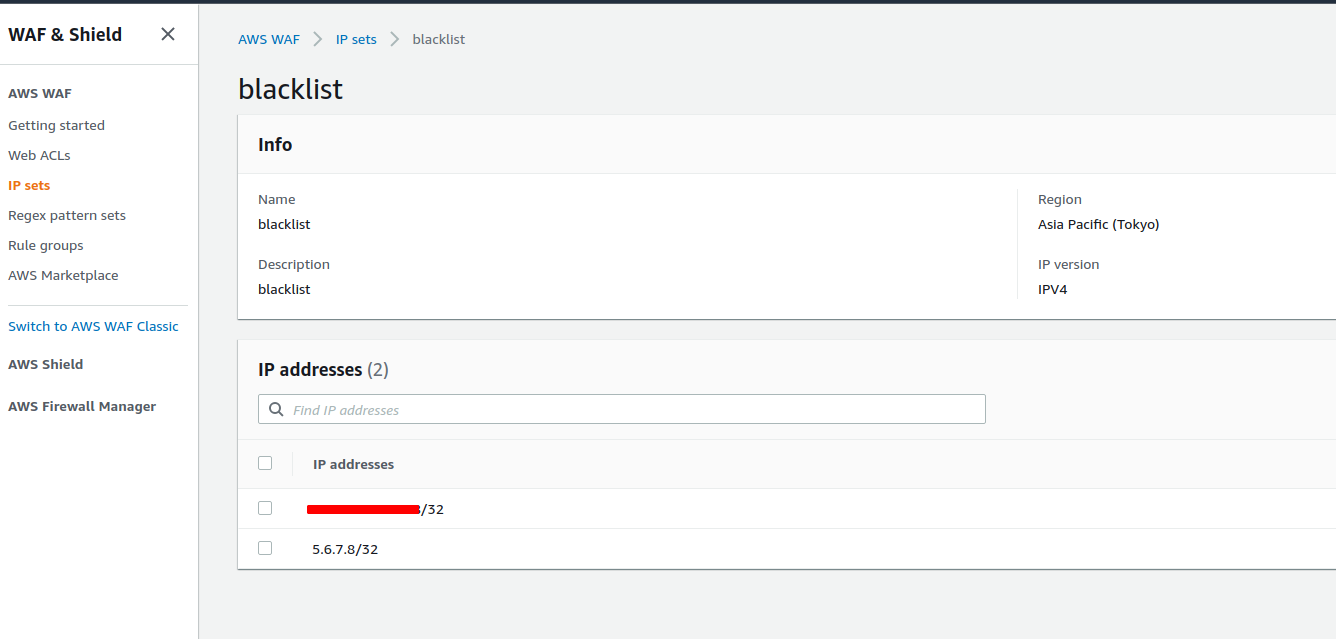
IPsetを作成する
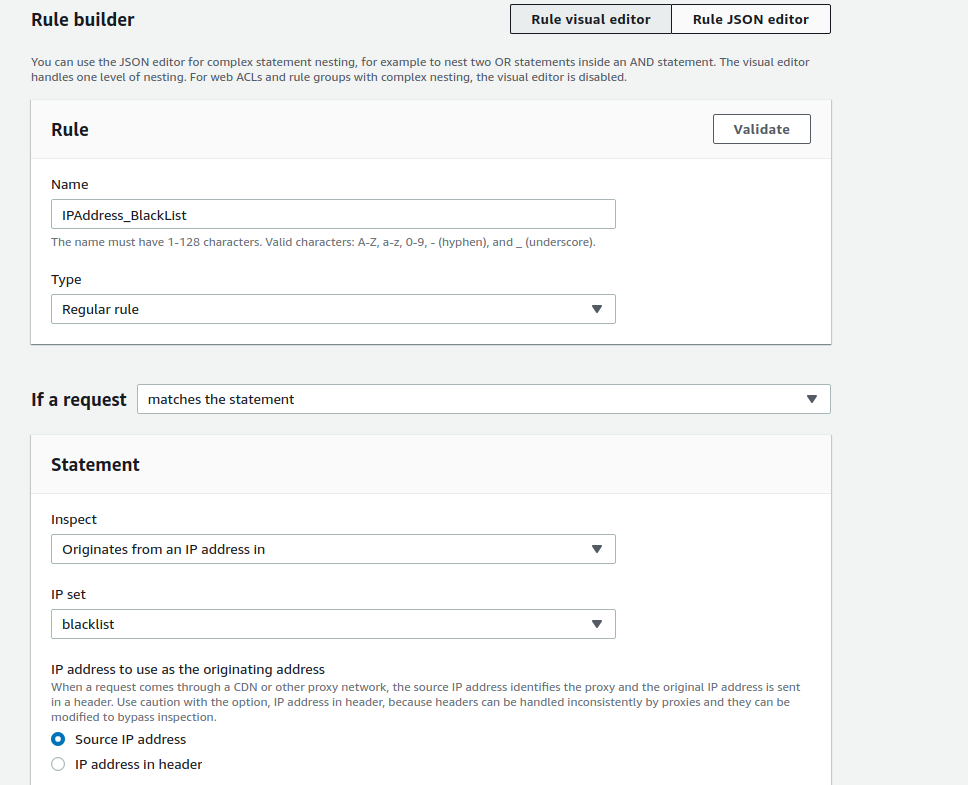
ルールを追加する
- Add rules → Add my own rules and rule groupsから追加する
- IPsetで作ったIPアドレスリストをアタッチ
- ActionはBlock
動作確認
- 接続しているALBへアクセスすると、ALBからの403で返ってくるようになる
yuta:~ $ curl -i https://dev2.vademic.jp/
HTTP/1.1 403 Forbidden
Server: awselb/2.0
Date: Sun, 29 Nov 2020 14:18:22 GMT
Content-Type: text/html
Content-Length: 118
Connection: keep-alive
<html>
<head><title>403 Forbidden</title></head>
<body>
<center><h1>403 Forbidden</h1></center>
</body>
</html>
Terraformコード
resource "aws_wafv2_web_acl" "example" {
name = "amelys-wafv2"
description = "wafv2 created from terraform"
scope = "REGIONAL"
default_action {
allow {}
}
rule {
name = "AWSManagedRulesCommonRuleSet"
priority = 0
override_action {
none {}
}
statement {
managed_rule_group_statement {
name = "AWSManagedRulesCommonRuleSet"
vendor_name = "AWS"
excluded_rule {
name = "SizeRestrictions_BODY"
}
excluded_rule {
name = "GenericRFI_BODY"
}
excluded_rule {
name = "CrossSiteScripting_BODY"
}
}
}
visibility_config {
cloudwatch_metrics_enabled = true
metric_name = "AWSManagedRulesCommonRuleSet"
sampled_requests_enabled = true
}
}
rule {
name = "AWS-AWSManagedRulesLinuxRuleSet"
priority = 1
override_action {
none {}
}
statement {
managed_rule_group_statement {
name = "AWSManagedRulesLinuxRuleSet"
vendor_name = "AWS"
}
}
visibility_config {
cloudwatch_metrics_enabled = true
metric_name = "AWS-AWSManagedRulesLinuxRuleSet"
sampled_requests_enabled = true
}
}
rule {
name = "IPAddress_BlackList"
priority = 2
action {
block {}
}
statement {
ip_set_reference_statement {
arn = aws_wafv2_ip_set.blacklist.arn
}
}
visibility_config {
cloudwatch_metrics_enabled = true
metric_name = "AWS-AWSManagedRulesIPAddressBlackList"
sampled_requests_enabled = true
}
}
tags = {
Automation = "Terraform"
}
visibility_config {
cloudwatch_metrics_enabled = true
metric_name = "AWSManagedRulesCommonRuleSet"
sampled_requests_enabled = false
}
}
// IPアドレスリスト
resource "aws_wafv2_ip_set" "blacklist" {
name = "blacklist"
description = "blacklist"
scope = "REGIONAL"
ip_address_version = "IPV4"
addresses = [
"1.2.3.4/32",
"5.6.7.8/32"
]
tags = {
Automation = "Terraform"
}
}